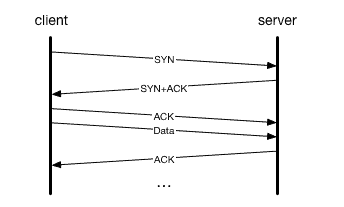
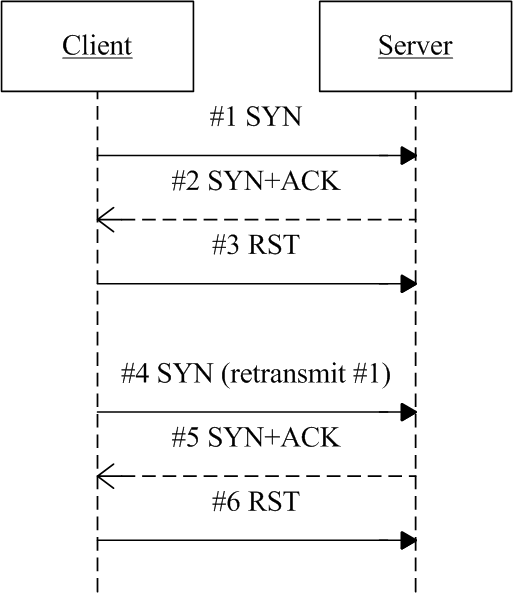
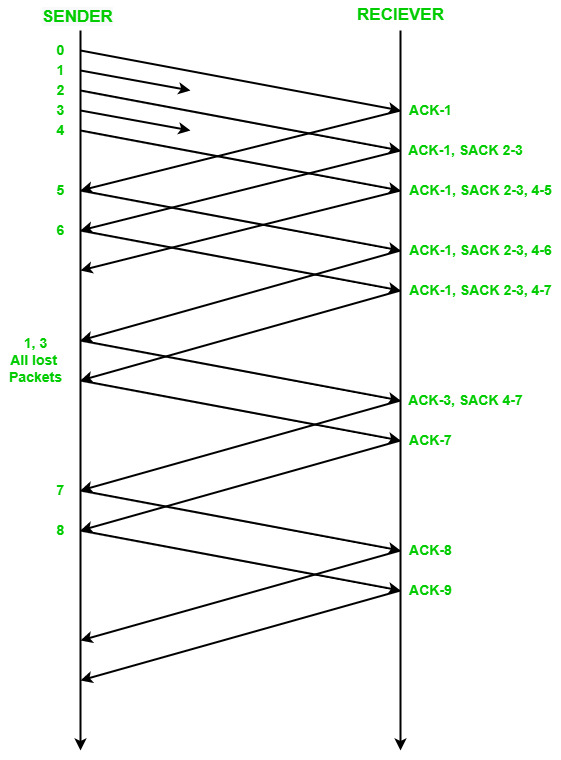
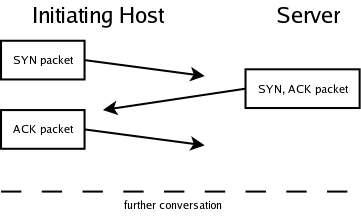
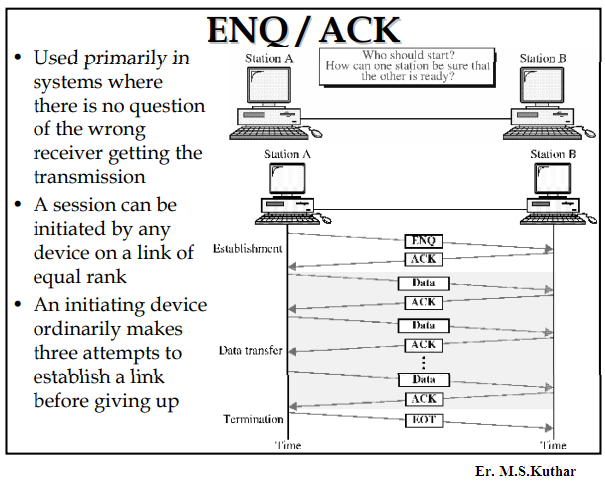
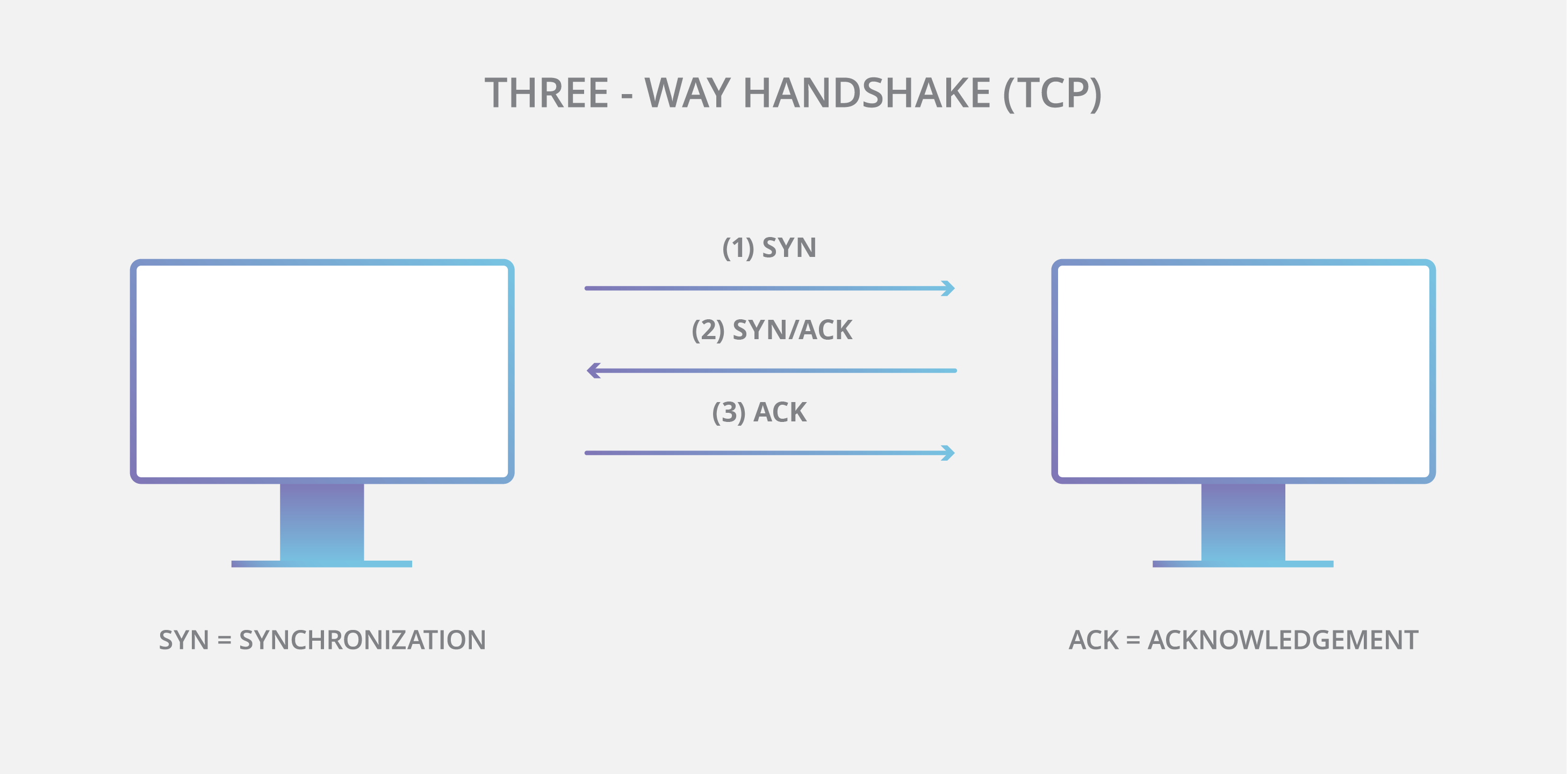
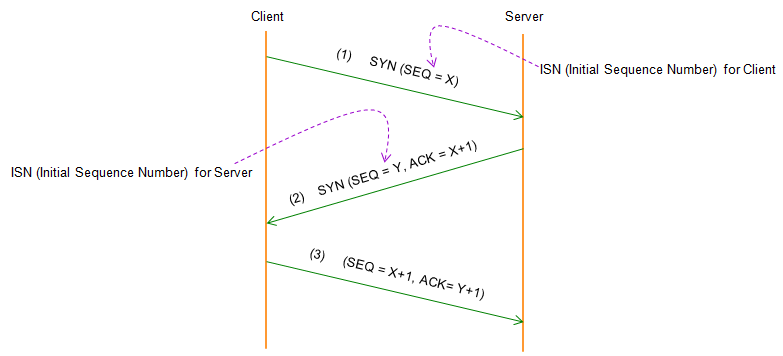
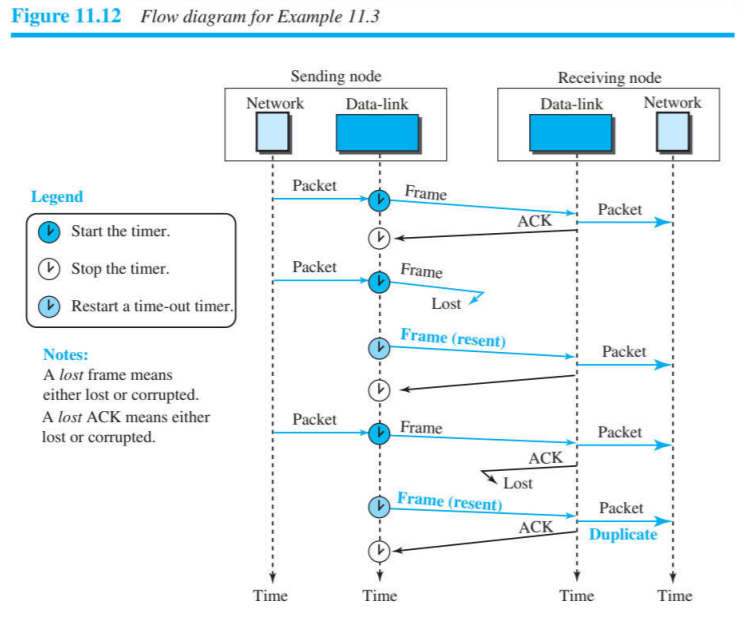
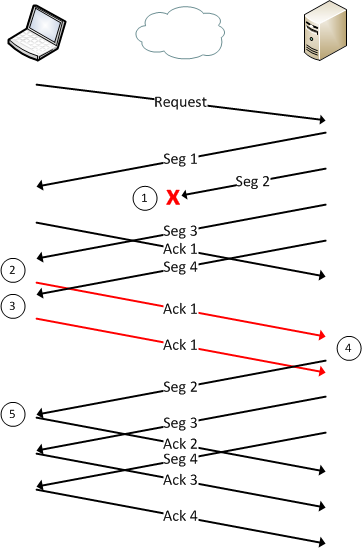
tcp - what's the acknowledgement number after retransmitting the missing segment - Network Engineering Stack Exchange

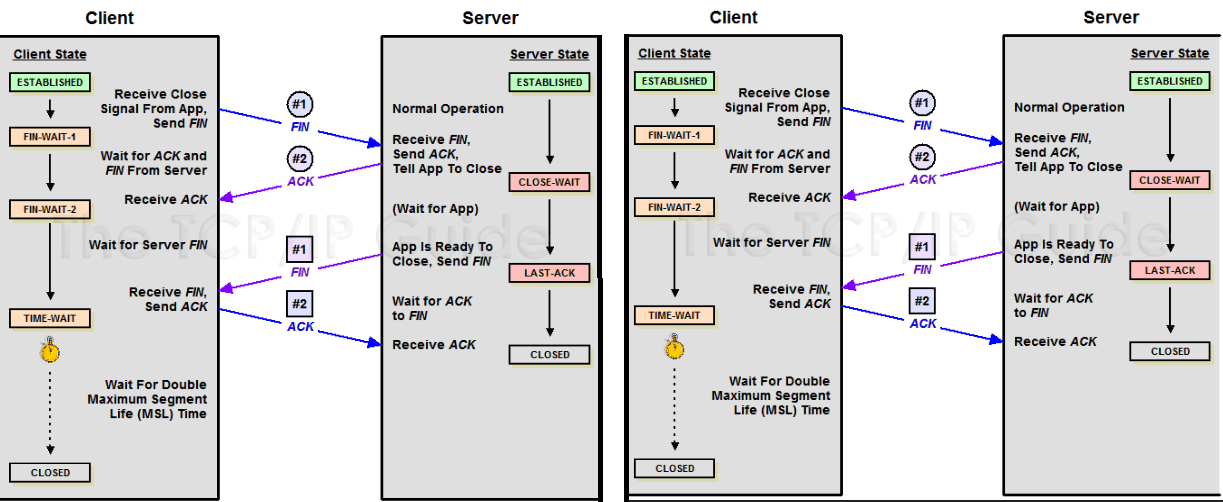
How to understand the sequence number of segments in TCP termination process in TCP/IP Illustrated, Volume 1: The Protocols (2nd Edition)? - Network Engineering Stack Exchange